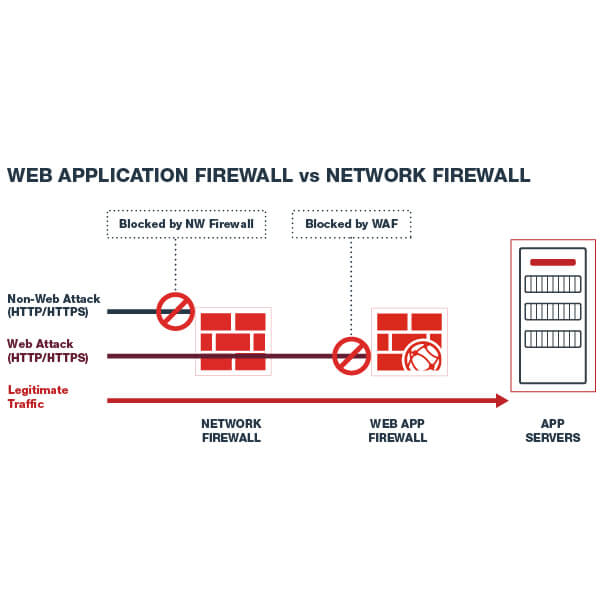
Web Application Firewall Vs. Network Firewall – What is the Difference?
Web application firewalls (WAFs) and network firewalls (NGFWs) are two types of security solutions. Both are important to deploy, but each has its distinct characteristics. For example, a WAF will protect your website against application-layer attacks, while an NGFW will protect your network from network-layer attacks.
WAFs protect against application-layer attacks
A web application firewall (WAF) can protect your website from attacks and add an extra layer of defense. These firewalls can monitor potential attacks and ensure your website meets regulatory standards. In addition, they provide alerts for suspicious activity. This makes your website more secure and responsive to potential attackers.
Early WAFs used static rules to analyze threats and generated educated guesses about web application behavior. They also tried to detect attacks by checking whether a request came from the same source and how fast it was received. However, their performance was insufficient for warding off evolving attacks, and the attackers had to devise new attack behaviors.
Web application firewalls are typically hardware or software devices that intercept HTTP traffic and filter bogus traffic. They are used with application security measures to prevent application-layer attacks and fraud. While a WAF won’t prevent every episode, it is beneficial for financial and e-commerce sites prone to data theft and fraud.
NGFWs can act as SSL termination proxies
NGFWs can act as SSL termination proxy servers for several reasons. First of all, they can inspect traffic at the application layer. However, as a result, they are often CPU-intensive. This means that they will cause performance degradation, especially when dealing with SSL/TLS encrypted traffic. Additionally, increased key lengths and complex ciphers can reduce their performance. Consequently, NSS estimates that SSL/TLS encrypted traffic will experience an average of 60% degradation, with a maximum of 95% loss.
Although NGFWs can act as SSL termination proxy servers, their performance can suffer. This is because they typically only see a fraction of malware and must be supplemented with bolt-on proxy functionality. In addition, NGFWs tend to underperform even when key features are enabled. Furthermore, they do not offer the scale and performance that cloud proxy servers can provide.
In addition, NGFWs use CRLs and OCSP to verify certificate revocation status. This ensures that the NGFW can decrypt SSL traffic, but the firewall must have some configuration to make this possible.
NGFWs inspect network layer packets
Next-generation firewalls (NGFWs) are network security devices that inspect network layer packets to detect and prevent known threats. These devices also support application-aware monitoring and deep packet analysis, which are used to identify malicious content and applications. These devices can also perform reputation and identity services to identify potentially malicious IP addresses and applications. These devices also help to reduce data breaches by limiting the use of non-business applications and prioritizing mission-critical applications.
NGFWs use a DPI algorithm to determine if a packet contains malicious code. Typically, this technique blocks traffic from an IP address or application. By inspecting Layer 7 boxes, NGFWs can detect malicious content hidden in files. This is an integral part of the application awareness features of NGFWs.
Advanced threats are designed to be challenging to detect with traditional firewalls. Next-gen firewalls must be able to inspect traffic at multiple OSI layers. They also need to be able to check traffic at the application layer, which is the layer where data interacts with the user.
NGFWs can inspect SSL traffic
NGFWs can inspect SSL traffic by analyzing the application layer. This is done through a process called deep-packet inspection. However, this process is computationally intensive. As a result, increased key lengths and complex ciphers can degrade performance. According to the NSS, performance losses for SSL/TLS encrypted traffic can range from 60 to 95%.
Next-generation firewalls also have extensive control over the applications in a network. They can identify and block malicious or safe applications through analysis and signature matching. These firewalls may also employ allowlists and signature-based intrusion prevention systems. They also use SSL decryption to determine which applications are safe and malicious. They can be deployed on a public cloud or a private network.