The Benefits of Implementing Identity and Access Management Solutions in Your Organization
IAM is crucial to meeting regulatory standards like GDPR, HIPAA, and Sarbanes-Oxley. It also prevents security risks when employees leave the company by automatically de-provisioning access privileges. IAM tools authenticate users, grant access to digital resources (such as software applications, hardware gadgets, and APIs), and track such accesses. This makes it possible to guarantee that an organization’s data is only accessible to the proper individuals and things.
Authentication
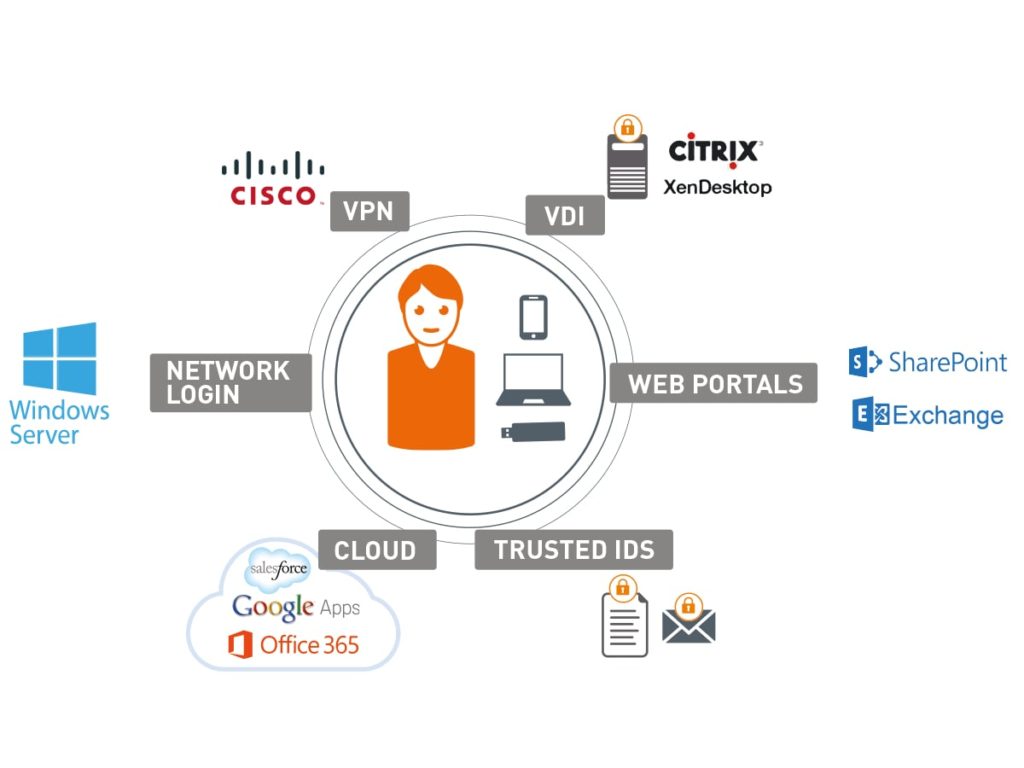
IAM solutions help ensure that the right people can access systems and files, like computers, software apps, and other IT resources. This is accomplished through authentication, authorization, and access control processes. The first step, authentication, is when a user must prove their identity by providing credentials like passwords or biometrics. IAM solutions typically have multifactor and adaptive authentication capabilities to increase security levels. Once a person has been authenticated, the access management process determines which tools they can use and what types of information they can view or edit.
This is done through a policy-based system that relies on roles, departments, or other established groupings of users. The system will also de-provision access privileges if employees leave the company or their role changes. This prevents a security gap where hackers could access the company’s sensitive data. It also saves time for employees by eliminating the need to manage multiple logins, thanks to single sign-on (SSO) technology.
Access Control
Identity and access management solutions provide the framework for establishing access to tools, software, systems, files, data, hardware, networks and facilities. This ensures that only authorized users handle the company’s information and are not doing more than their credentials permit. Authentication methods used by IAM systems include multifactor authentication and adaptive authentication, which require more than one element of proof of identity to confirm a user’s credentials.
Using these methods reduces the risk of password hacking and increases security by ensuring that the certificates requested are contextually relevant to the user and the situation. You may learn more about the comprehensive purpose of IAM and how it can benefit any firm by visiting Tools4Ever.com. IAM solutions automate many critical identity and access-related functions, like managing users’ account information, requiring periodic password updates and verifying that the correct person is using the right login at the right time. This helps to improve productivity, minimize frustration over passwords and frees up expert IT team members to shift their focus on addressing more complex IT issues.
More tools are needed to manage employee access to firm data and systems than firewalls and passwords. IAM, or identity and access management, is a complete security system that uses multifactor authentication, automates provisioning and de-provisioning procedures, and analyzes user behavior for indications of cyberattacks. The core of IAM is authorization, which grants full or partial access to applications, files, services, and systems based on the person’s role in an organization. For example, a manager may view but not modify employee information or company financial data.
Role-based access control also ensures that employees have permission to complete their work without leaving a security gap for hackers to exploit. IAM solutions reduce the number of help desk calls for password resets and other identity-related issues, allowing IT teams to spend time on higher-priority tasks. They also support compliance with industry regulations and withstand regulatory audits by maintaining consistent, centralized management of access privileges across all systems, devices, and applications.
Reporting
The digital workplace requires users to access various technology systems across the enterprise. This can be challenging for security admins, who must ensure that each user can access the tools and data they need for their role and no more. An identity management solution can help with these challenges. IAM solutions can control access to applications and information by creating a single digital identity for each user, improving security posture and efficiency.
In addition, these solutions can stop password reuse by guaranteeing that each new user has their credentials. Users may no longer need to reset passwords or submit help desk requests. As a result, they are freeing security professionals to work on other projects. These systems can also recognize potential security threats like unsuccessful login attempts or shady file activity and take appropriate action. By doing this, the danger of security breaches can be greatly decreased.



