Intro To Directory Listing, and how does it work?
A list of files and folders that you are directory exploring appear when you enter a website through a web browser instead of a webpage. This error message is the result of the web server’s inability to simply display web pages on your website. Not only that, but the files and folders on your site could also have their contents hacked. The absence of any index files (such as index.html, index.php, and so on) in the directory in question is a frequent cause of this.
When a browser sends a request for access to a web page to a web server for processing, the server handles the request. Depending on the situation, a web server can be programmed or instructed to prioritise some websites to display first when requests to display web pages are received.
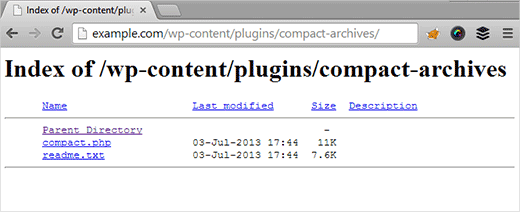
When a browser initiates a request, the index file (“index.html” or “index.php”) is usually the first thing the web server puts up. In the absence of an index file, the web server shows the entire contents of the directory that the browser requested. This means that you can see all of the files and directories in the directory!
Most web servers are set up so that the contents of your directory (also known as directory itemising) aren’t displayed. You must ensure that directory browsing is disabled on your WordPress website. If you don’t disable it, it’ll be as if you’re delivering your website to hackers on a silver platter!
What is Directory Listing?
When enabled, the web server function known as “directory listing” displays the contents of directories without index files (e.g. index.php or index.html). Therefore, even if a directory contains files from a web application, the web server will return a directory listing if a request is made to a directory on which directory listing is enabled and there is no index file, such as index.php or index.asp.
As a result, there is a problem with information leakage, and attackers may use this information to construct further attacks that take use of direct impact vulnerabilities like XSS. The output of the directory listing function resembles that of the operating system’s dir or ls command, as seen in the image above. Issues with directory listings are the kind from which an SSL certificate won’t shield you. The good news is that an online vulnerability scanner that is automated can quickly find these kinds of problems.
What data is exposed by directory listings, and what are the risks?
Assume that the hidden folder has directory listing enabled and contains a backup copy of the file config.php that contains the database connection information. When an attacker attempts to access the secret folder directly, such as via http://www.example.com/secret/, after discovering it through crawling or fuzzing He has access to the backup files, which contain the database connection information, and can download them. Now that the attacker has access to the database connection information for the web application, they may use these credentials to harm the database or the web application.
the best way to stop directory listings
Disabling directory listing is advised as a security best practise. By adding an empty index file (index.php, index.html, or any other extension your web server is set up to parse) to the directory in question, you can deactivate directory listing. Even so, this is frequently not the ideal course of action because such files are frequently overlooked, like when moving a web application from a development environment to a production one or when new folders are introduced. Therefore, as described in this article, you should develop a long-lasting and secure solution by deactivating directory listing at the web server level.
Why is it necessary to disable directory browsing?
An information disclosure subject would be a web server configured to display all of the contents of your website. An attacker could use Thich to plan an attack on your WordPress blog.
How would he be able to accomplish this? So, here’s the scenario. Let’s imagine you have a website with the following domain name – www.yoursitename.com – and you create a personal folder. If this website’s directory browsing is enabled by default, a hacker can access all of the files under personal by typing http://www.yoursitename.com/personal/ into the browser.
Consider the abundance of information available to a hacker who could undoubtedly exploit flaws in your files. An attacker might also examine the essential and secret contents of restricted files within the directory by browsing the directory. And even the file hierarchy, which will provide him with crucial information about the website’s configuration. If the directory that houses these files has directory browsing allowed by default, he can use all of these to locate the vulnerabilities in your website – WordPress plugins, themes, core, and so on.
Disabling directory browsing is a must-have security feature.
Disabling directory browsing isn’t a security measure in the sense that it won’t make your site any safer. You’re simply protecting your files from being exposed to an attacker. While this is extremely important, it is only security through obscurity. And it’s not even close to being enough to keep your website safe.
A hacker can come up with a slew of new ways to exploit your site’s flaws. So this step merely ensures that your website will not be given to him on a silver platter! That example, accessing all files in a directory with a single request is usually not possible.
So disabling directory itemizing/browsing is essential to your website’s safety, however, it can not make sure that your website is secure. You’ll need to take certain website hardening measures, like installing a firewall and generating strong usernames and passwords, to do this. Installing security plugins that, among other things, can scan and clean your website (in case there is malware).
Find out if directory browsing is available on my site.
You’ll want to enter the files in your website to see if any random individual can browse your directory. Using an FTP client is the simplest way to accomplish this. For the sake of this article, we’ll be using the FileZilla FTP client. If you don’t already have FileZilla, you can get it from here.
To make the process go more smoothly, keep the following things in mind before you begin:
Login credentials for FTP (username, host server, password, port).
Step 1: Open FileZilla and log in using the FTP credentials listed below, then select Quickconnect.
Once you’ve connected to the server, the Remote Site section will display the contents of your website, as shown in the image below.
Step 2: Next, in your Local Site portion (as shown by the arrows), in the left side panel, create a dummy folder. As shown below, we called our dummy folder Test.
Step 3: Drag the Test folder from the Local Site section to the Remote Site section (i.e. from the left side panel to the precise side panel). This will be placed in the remote website’s public.html subdirectory.
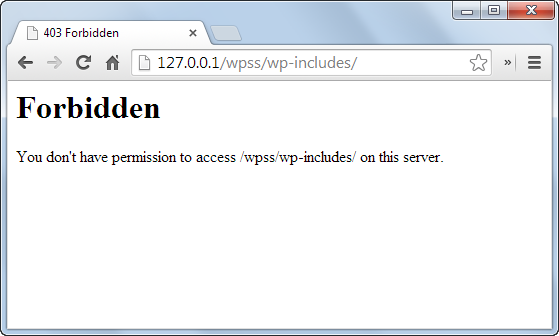
Step 4: After you’ve created a parent directory/folder in the public.html section, you can test if directory browsing is enabled or disabled by putting the following into your browser:
http://www.yoursitename.com/Test/
Because the name of the dummy folder we had established was Test, we typed it. Instead, you’d be entering in the name of the folder you’ve established. We couldn’t access the content of the Test directory because directory browsing was disabled in our situation. Rather, the browser displayed an error notice, preventing access to the directory.
At the web server stage, disable directory browsing –
It’s possible to finish disabling directory browsing by using
- Either use your Web Host Manager to update the configuration file for your web server, httpd.conf.
- Alternatively, you can use the FTP client to upload “.htaccess” directly to your website.
- Alternatively, you can change the ‘httpd.conf’ file.
The ‘httpd.conf’ file, on the other hand, is a configuration file that may require root access to the web server to update. Web servers now come in a variety of flavours: apache, nginx, litespeed, and so on. Changing the ‘httpd.conf’ file on any of those web servers necessitates root access, as we previously discussed.
If you’re self-hosting your website, you’ll have the necessary root access. If you are using a web host to host your website (managed or shared hosting), you will need to contact your web host for the base entry. Your web host’s decision on whether or not to provide this information is up to them; some may agree, while others may not. As a result, double-check with your web host on this.
After you’ve obtained the requisite root access, you’ll be able to log in as the primary user to cPanel/ control panel or Web Hosting Manager (WHM). For further instructions on how to alter the settings of your Apache web server’s ‘httpd.conf’ file, see this article.
How to Disable Directory Browsing in Cpanel
Indices in the File Manager (method 2)
Step 1: To disable directory indexing, navigate to the cPanel Index Manager.
This procedure is similar to the one described above until Step 3, when you launch File Manager after authenticating into your web server. When you right-click on the folder you want to block directory browsing for, rather than selecting Change Permissions, select Manage Indices as shown below.
Step 2: When you click on Manage Indices as shown below, you will be transported to the Index page.
After that, select No indexing. Keep track of the changes you’ve made. Your website’s directory browsing will be disabled as a result of this.
Using.htaccess, you may prevent your website from being listed in a directory.
If you don’t put a “index.html” file in a new directory (or folder) on your website, you might be surprised to learn that your visitors can get a directory listing of all of the contents in that folder. For example, if you name a folder “incoming,” you may view all of the items in that directory by typing “http://www.example.com/incoming/” into your browser. There is no need for a password or anything else. This post will show you how to set up your web server so that it does not display a directory itemising by default.
Prerequisites
An Apache Web Server is required for your website.
Your website must be hosted on an Apache web server in order for the strategy outlined in this article to operate. This is almost certainly true of practically all web pages on the Internet, thus you appear to have met this condition. In most cases, if your web server (the computer that your website is running on) is running Linux or FreeBSD, it’s running an Apache server. If your server is running Windows, it’s possible that your website isn’t using Apache.
However, nothing will be misplaced. You can still get the same result by employing a different approach. As an alternative, read How to Prevent a Directory Listing of Your Website Without Using.htaccess. (Note that I’m referring to the computer that hosts your website, not your own computer.) Inquire with your web host if you’re not sure what type of server your website is on.)
.htaccess Server Overrides Must Be Enabled By Your Web Host
Your web host must have enabled server overrides in addition to being hosted on an Apache web server. This feature allows you to make changes to the web server configuration from your own personal website. In practise, this usually means that your website is hosted on a paid server rather than a free one. Free web providers often do not allow web sites hosted on them to change the behaviour of the web server.
Both of the above prerequisites must be met; otherwise, you will not be able to complete the tasks discussed in this article efficiently.
Is it a security measure to hide your directory listing from public view?
Protecting your directories from being listed by your website’s visitors does not make your website safer in and of itself. At best, it’s security by obscurity. That is, you expect that by hiding things from view, malicious guests up to no good won’t be able to just request a list of all of your files. It doesn’t stop them from accessing these files directly by name. While you should take various security measures to protect your website, it is still a good practise to not allow your directory to be displayed by default. That way, at the very least, you’re not making it too easy for others to scan your website for flaws. This is especially true if your website has third-party scripts (equivalent to, for instance, you run a blog). It’s critical to comprehend this so that you don’t rely solely on this way for safety.
Disabling directory listing in all web projects
To disable directory listing on the Tomcat web server, open the conf/web.xml file in the directory where Tomcat is installed. In our test on Windows 10, the default installation directory was “C:\Program Files (x86)\Apache Software Foundation\Tomcat 9.0” <servlet> <servlet-name>default</servlet-name> <servlet-class>org.apache.catalina.servlets.DefaultServlet</servlet-class> <init-param> <param-name>debug</param-name> <param-value>0</param-value> </init-param> <init-param> <param-name>listings</param-name> <param-value>false</param-value> </init-param> <load-on-startup>1</load-on-startup> </servlet>Find the listing part of the <param-name> value in the <init-param> tag. As you can imagine, <param-value> is the determining factor for us in this section. If this field is true and you want to disable directory listing, change this field to false. You can directly copy and modify the following code: <servlet> <servlet-name>default</servlet-name> <servlet-class>org.apache.catalina.servlets.DefaultServlet</servlet-class> <init-param> <param-name>debug</param-name> <param-value>0</param-value> </init-param> <init-param> <param-name>listings</param-name> <param-value>false</param-value> </init-param> <load-on-startup>1</load-on-startup> </servlet>
Disabling directory listing in a specific web project
In the first method, we configured a general setting that applies to all the web projects running on the server. In this method, we will configure it so that it only affects the website we changed. Open the web.xml file for the relevant web project and add the following code: <servlet> <servlet-name>DefaultServletOverride</servlet-name> <servlet-class>org.apache.catalina.servlets.DefaultServlet</servlet-class> <init-param> <param-name>debug</param-name> <param-value>0</param-value> </init-param> <init-param> <param-name>listings</param-name> <param-value>false</param-value> </init-param> <load-on-startup>1</load-on-startup> </servlet> <servlet-mapping> <servlet-name>DefaultServletOverride</servlet-name> <url-pattern>/</url-pattern> </servlet-mapping><servlet> <servlet-name>DefaultServletOverride</servlet-name> <servlet-class>org.apache.catalina.servlets.DefaultServlet</servlet-class> <init-param> <param-name>debug</param-name> <param-value>0</param-value> </init-param> <init-param> <param-name>listings</param-name> <param-value>false</param-value> </init-param> <load-on-startup>1</load-on-startup> </servlet> <servlet-mapping> <servlet-name>DefaultServletOverride</servlet-name> <url-pattern>/</url-pattern> </servlet-mapping>The default servlet was overridden with the above change. Now, the website we made this change on will run independently of the setting we configured in the first method.
Disabling directory listing on Nginx
The directory listing feature on Nginx is controlled by the ngx_http_index_module. Directory listing is disabled by default on the Nginx configuration file. However, it is possible to disable directory listing if it was enabled because of a regression or configuration changes. The Nginx parameter autoindex is used together with the location segment to enable or disable the directory listing feature. The default configuration file of a Nginx server is called nginx.conf and can be found in /usr/local/nginx/conf, /etc/nginx or /usr/local/etc/nginx. If the default value has been changed, you can see a setting similar to the following: server { listen 80; server_name domain.com www.domain.com; access_log /var/………………………; root /path/to/root; location / { index index.php index.html index.htm; } location /somedir { autoindex on; } }In this section, the determinant parameter is autoindex on; as we mentioned above. In the above example, the directory listing is configured only for the somedir directory. If no directory is specified (e.g. location / {autoindex on;}), the rule will be applied to all the folders. To disable directory listing, we need to switch the value of the autoindex to off. Do not forget to run the below command in order for changes to go into effect: service nginx restart
How to Avoid Being Listed in a Directory
Using FTP or SFTP software, connect to your website. Look in your website’s top web directory, where you’ll put your property web page, for a file called “.htaccess.” Obtain it to your pc if it exists. If it doesn’t exist, double-check that it isn’t hidden from view. This can only be done from within your FTP application. Depending on the programme you’re using, you may need to look for a setting that says “display hidden files.” You’ll have to allow the “Force showing secret files” line in the Server menu in one programme, specifically FileZilla, even though the programme reveals it by default in my experience.
Another option is to access your website directly from your web host’s management panel. Most, if not all, commercial web servers provide a way for you to view, add, and download files from your online directory using your computer browser. If your web server offers the option to “display secret files” or anything similar, make sure you enable it. You should be able to locate and download your current.htaccess file using your host’s web interface. Don’t worry if you can’t find any.htaccess files in the primary site directory despite your best efforts. It’s fairly common for a website to be without one. You’ll just need to make a new one later. However, if one exists, it is critical that you obtain it so that we can add to the file’s settings rather than overwriting them.
Make a copy of the.htaccess file for safekeeping.
If you were successful in locating and retrieving the.htaccess file from your website, make a backup copy on your computer. That is, make sure you have two versions of the.htaccess file on your computer: one that you’re about to alter and one that is in perfect condition. The backup is useful in case you make a mistake later on.
Make a.htaccess file or open one that already exists.
If you’ve managed to obtain the.htaccess file, open it in a plain text editor (e.g., an ASCII text editor) such as Notepad (for Windows users), and scroll to the file’s end, on a clean line. If none exists, use the editor to create a new, blank document. The rest of this text will presume that you’ve already opened the editor with the.htaccess file open, or that you’ve started with a blank document if no.htaccess file exists. WARNING: Do not create or edit your.htaccess file with a word editor like Word, Office, or WordPad. For this purpose, you should also avoid using a WYSIWYG (What-You-See-Is-What-You-Get) online editor. Your website will mysteriously stop working while you add the file to your web server if you perform both of these things. This is critical. There are no exceptions to this rule.
Indexing is disabled.
To your.htaccess file, add the following line.
-Indexes -Options
After you’ve entered the “Options -Indexes” phrases, make sure to use the ENTER key (or the RETURN key on a Mac) to end the file on a clean line.
Getting the File Saved and Uploaded
Save the file once you’ve finished deactivating directory listing in the.htaccess file. If you’re using Notepad to create a new file, make sure you save it as “.htaccess” with quotes and everything. If you don’t include the quotations, Notepad will automatically append a.txt extension to your filename. Also, make sure the filename is strictly.htaccess, which means it starts with a full stop (“period” in US English) and is written entirely in small characters (lowercase). There is no other name that will suffice. Then, using an FTP/SFTP programme (or your web host’s control panel), upload the file to your web server.
Test Your Website
Make sure that your website is still operational after you import any modifications that you make to the.htaccess file whenever you make a change to it. When I say this, I am not joking at all. Everything that the server performs in connection with your website, including caching and redirects, is controlled by the.htaccess file.
It only takes a simple oversight to render your entire website inaccessible to users. When I say, “check your website,” what I mean is that you should double-check not just that a directory that does not contain “index.html” cannot be listed, but also that your primary web page and a few other sites are still loading. This is what I mean when I say, “check your website.” In the event that something goes wrong with your website, you can fix it by deleting the.htaccess file and trying to access it again. If the positioning already had a.htaccess file, the backup copy should be used to replace it.







Very useful. Thank you
Keep reading and sharing